Security Information and Event Management Solution
Security Information and Event
Management (SIEM)
Is Your SIEM Effectively Catching Threats?
What is SIEM?
While security information and event management (SIEM) solutions have been around for over a decade, and have evolved significantly over that time, the core functionality still acts as the most effective foundation for any organization's technology stack.
At its most fundamental level, a SIEM solution enables an organization to centrally collect data across its entire network environment to gain real-time visibility into activity that may potentially introduce risk to the organization.
Using SIEM technology to achieve visibility into network activity helps organizations address issues before they become a significant financial risk. It also helps operations better manage company assets.
See a SIEM in Action
LogRhythm can help you tell a cohesive story around user and host data, making it easier to gain proper insight needed to remediate security incidents faster.
In this demo inspired by real-life events, watch a security analyst use our NextGen SIEM Platform to detect a life-threatening cyberattack on a water treatment plant.
How Do SIEM Solutions Work?
The core set of capabilities for a SIEM solution includes data collection, parsing (or normalizing) data, and correlating that data to identify suspicious or problematic activity. This processing and enrichment of data enables all forms of data analysis and can have a direct impact on how effectively an organization can search and access its data.
Once the data has been ingested and normalized, the SIEM software correlates events across all of the data in aggregate to identify patterns of compromise and alert the end user to suspicious activity.
SIEM technology can reside either on-premise (on your own hardware) or in the cloud (on someone else's hardware) and collect data from a massive variety of data sources.
The SIEM Essentials
- Log Management: Collect, normalize, and aggregate log data to deliver efficient data access and management
- Real-Time Monitoring: Observe activity at the exact moment it occurs within your network environment
- Incident Investigation: Search and drill down on logs to further investigate a potential incident
Benefits of Leveraging SIEM as Your Security/IT Foundation
SIEM solutions map to modern operational needs, delivering real-time visibility, efficient and secure data access, streamlined workflows, a unified user experience, and the ability to customize how you manage your environment based on the demands of the organization.
Some key benefits include:
Value for Security and IT Operations
- Effective collection and normalization of data to enable accurate and reliable analysis
- Real-time visibility across your environment to quickly identify and prioritize potential issues
- Ease of accessing and searching across raw and parsed data for investigation and compliance
- Ability to map your security and IT operations to existing frameworks such as NIST and MITRE ATT&CK
Broad Integration Across Security and IT Vendors
- Support for integration with hundreds of security and IT solutions to further extend SIEM capabilities and data collection
- Central management of all security related solutions that ties together disparate solutions to provide a single pane of glass
Compliance Adherence, Enforcement, and Reporting
- Ensure compliance adherence with real-time visibility and notifications to ensure awareness of all compliance-related activity
- Prebuilt compliance modules automatically detect violations as they occur to remove the burden of manually reviewing audit logs
Learn How LogRhythm Can Help Your Team
Let one of our experts review your use cases and demonstrate how the LogRhythm NextGen SIEM Platform can help you detect and respond to threats faster than ever before.
The Evolution of SIEM Software
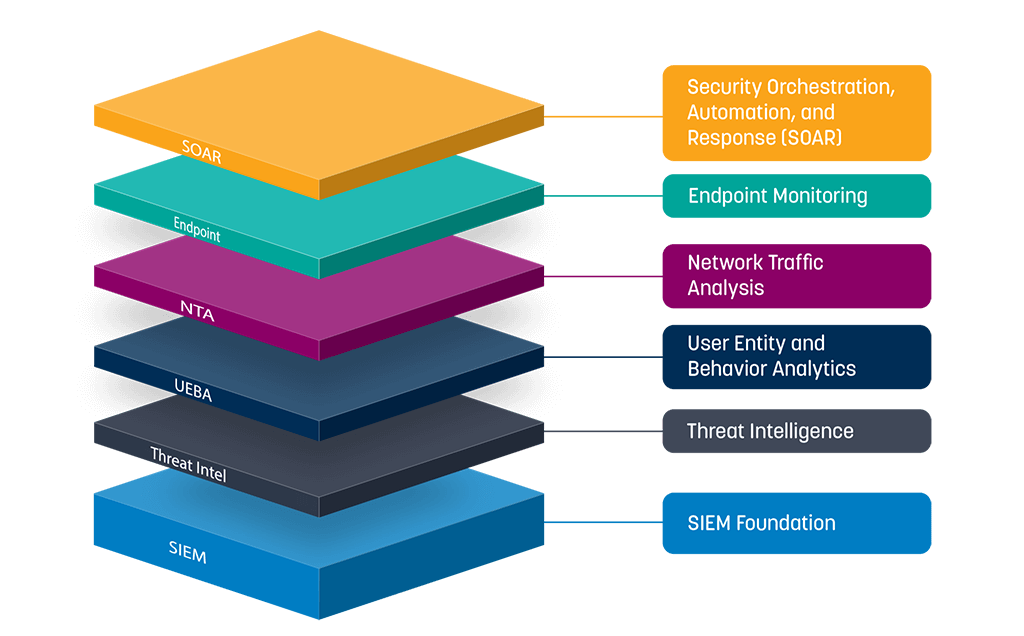
As SIEM software has transformed over time, the core components continue to provide value, while new, innovative technology — such as automation and new analytical techniques — has been built on top of the traditional SIEM foundation to provide the most comprehensive approach to reducing risk across an organization.
This evolution of capabilities and features is often referred to as "next-gen SIEM." The deployment of a next-gen SIEM solution delivers enhanced methods for securing data and solidifying operational excellence. In "An Evaluator's Guide to NextGen SIEM," SANS provides specific criteria for advancing to the next evolution of SIEM technology.
There are three key elements that make up the foundation of all leading SIEM solutions:
- Data quality: Effectively ingest and normalize data to enable more precise search and analysis
- Scalability: Scale in parallel to an organization's growth to collect, normalize, and analyze an increasing quantity of data
- Flexible deployment options:
- SaaS
- Cloud deployment
- On-premise
The integration of threat intelligence with foundational SIEM capabilities provides additional threat context that can help deliver faster mean time to detect (MTTD) and can ease some of the burden of incident investigation.
Threat intelligence feeds typically include malicious:
- IPs
- URLs
- Domain names
- Email addresses
- Filenames
- Hashes
- Registry keys
- DLLs
Behavioral analysis provides a unique look at the activity of users and network entities to be able to prioritize and address behavior that shows significant deviation from normal behavior. UEBA solutions use machine learning (ML) to determine both the baseline (normal behavior) of each user and entity and the significance of any activity that deviates from that baseline.
UEBA Use Cases
- Data exfiltration
- Service account misuse
- Insider access abuse
Analysis of network traffic and packet data delivers visibility into the communication methods and patterns between networked devices. NTA solutions can be leveraged as a set of rules, looking for specific patterns and behavioral outliers, or as an effective means for performing threat hunting.
NTA Use Cases
- Application usage
- Data exfiltration
- Bandwidth utilization
Endpoint monitoring enables operations to track activity on an endpoint that includes the viewing, creation, modification, and deletion of files. This ability to track file access and modification is often delivered through an endpoint solution that includes file integrity monitoring (FIM) as part of the feature set.
Endpoint Monitoring Use Cases
- Forensic analysis
- Data exfiltration
- Sensitive data access
SOAR is an underlying set of capabilities that increase operational efficiency and collaboration across all the other layers of a next-gen SIEM platform. These capabilities include case management and contextualization for incident investigation, and playbooks for streamlining operational workflows.
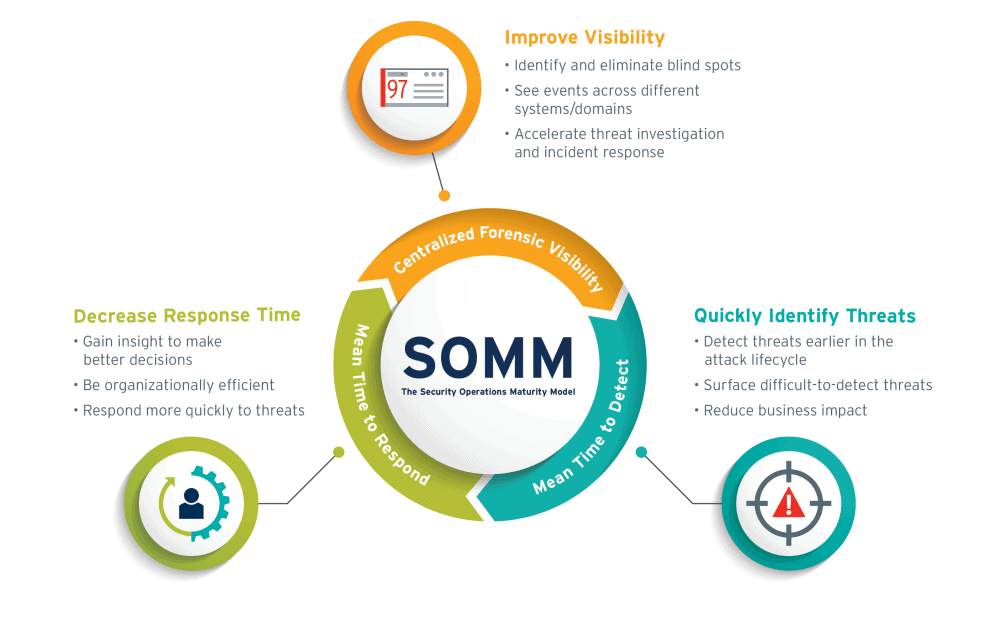
Benchmark Your SOC with the Security Operations
Maturity Model (SOMM)
With all of the innovation that has occurred within the SIEM solutions space, it can be difficult to determine the right set of capabilities to reduce risk within your own organization. LogRhythm's Security Operations Maturity Model (SOMM) provides a benchmark to measure your current security posture and better understand how to progress your operational readiness.
The LogRhythm NextGen SIEM Platform
LogRhythm's NextGen SIEM Platform delivers comprehensive security analytics, UEBA, NTA, and SOAR within a single, integrated platform for rapid detection, response, and neutralization of threats. Our platform strengthens the maturity of your security operation, better aligning your technology, team, and processes. With LogRhythm, your team is ready to face whatever threats may come its way.
Ready to Learn More?
Schedule a personalized demo with a security expert to see LogRhythm in action.
Security Information and Event Management Solution
Source: https://logrhythm.com/solutions/security/siem/